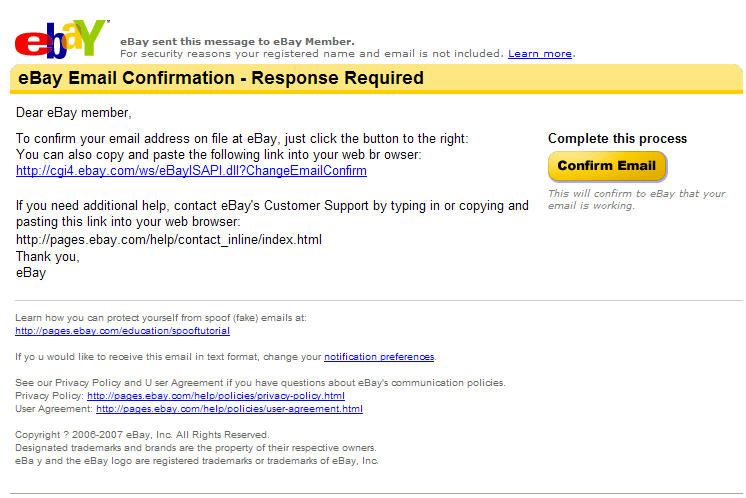
This message arived today – form an Ebay – I mean, Eday member:
With Outlook, Eday is easily read as Ebay…
Fake of course, sent to obtain credentials.
The header shows it’s origin: Australia – given the names, I’d say Melbourne:
Return-Path: member@eday.com
Received: from mail.southern-ro.com.au (203.46.24.242)
by xxxxxxxx.grootersnet.nl (V5.6-9, OpenVMS V8.3 Alpha);
Thu, 30 Aug 2007 13:40:27 +0100 (CET)
Received: from User ([195.84.14.70]) by melbserver.southern-ro.com.au with Microsoft SMTPSVC(6.0.3790.3959);
Thu, 30 Aug 2007 21:40:16 +1000
Reply-To: <member@eday.com>
From: "member"<member@eday.com>
Subject: message from member
Date: Thu, 30 Aug 2007 13:40:15 +0200
MIME-Version: 1.0
Content-Type: text/html;
charset="Windows-1251"
Content-Transfer-Encoding: 7bit
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
Bcc:
Return-Path: member@eday.com
Message-ID: <MELBSERVERAtC33BcZY00000e29@melbserver.southern-ro.com.au>
X-OriginalArrivalTime: 30 Aug 2007 11:40:16.0643 (UTC) FILETIME=[891CAD30:01C7EAFA]
that is: from address 195.84.14.70, and this is NOT an Ebay address, nor is the mailserver that connected (203.46.24.242). Nor would Ebay use Outlook Express. In other words: it is a basic PC. no TO: line either, I wonder how the message got here in the first place.
No name in the message – which is not like ebay would do it.
Almost all links that could require a login, refer to a site at oberleitner.biz. Even the ones wheer you could signal or learn about abuse:
Always remember to complete your transactions on eBay - it's the safer way to trade.</B><BR><BR>Is
this message an offer to buy your item directly through email without
winning the item on eBay? If so, please help make the eBay marketplace
safer by reporting it to us. These external transactions may be unsafe
and are against eBay policy. <A href="http://www.oberleitner.biz/cache/ws/eBay_com_Verify_your_eBay_account_files/" target=_blank><FONT color=#003399>Learn more about trading safely</FONT></A>
A bit more down:
<B>Always remember to complete your transactions on eBay - it's the safer way to trade.</B><BR><BR>Is this message an offer to buy your item directly through email without winning the item on eBay? If so, please help make the eBay marketplace
safer by reporting it to us. These external transactions may be unsafe and are against eBay policy. <A href="http://www.oberleitner.biz/cache/ws/eBay_com_Verify_your_eBay_account_files/"
target=_blank><FONT color=#003399>Learn more about trading safely</FONT></A>
and
Learn how you can protect yourself from spoof (fake) emails at:<BR><A href="http://www.oberleitner.biz/cache/ws/eBay_com_Verify_your_eBay_account_files/" target=_blank><FONT
color=#003399>https://pages.ebay.com/education/spooftutorial</FONT></A>
It looks like Oberleitner.biz’s business is getting user credentials. Or it’s domain is abused.