Bandwith management
My son has bought a laptop some weeks ago and now he’s consuming all bandwidth downloading. At some point the software he uses had over 4000 sessions open, causing a severe access problem – both from outrside as inside. Most of this traffic seems to be outgoing – synchronisaton, probably?.
First, I squeezed the number of sessions from his laptop to a max of 200 – that helped somewhat, but still the outgoing traffic took almost all available space on the 1Mb channel. So this evening, I limited his upload bandwidth to 200Kb – and that caused his download speed to be much lower as well.
This shows immediately in the traffic graph:
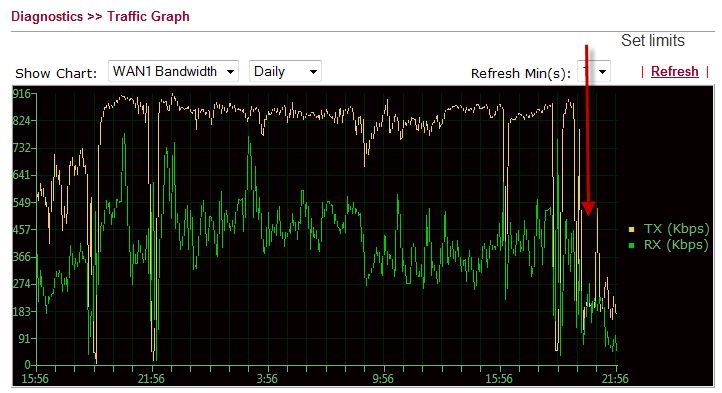
Stupid program ….
Another side effect is that the SYSLOG files grows VERY FAST. Where it took a few days – or a week – to exceed 25000 blocks, now it took just severakl hours…Each day, the log grows to a 125.000 blocks. This squeezing may decrease the growth as well – less traffic means less entries.
Space is not a real issue, but I’ll have to keep a keen eye on the size…
Blocking abuser
Another ability the router / firewall offers is blocking access from specific addresses – or subnets. That allows me to block a complete subnet: 69.25.7.0. This network offers the possibility of DoS attacks over Trace_rt – that doe occur severely at tgimes, overfilling my mailbox by the number of alerts due tgo these attemps, from the network, ending by a number ending in a mulitple of 4. We’ll see what happens next. Of course, this blocking is logged.
BTW: The owner – according WHOIS – has been notified of the abuse. But I didn’t receive confirmation – yet.
Disk trouble – continued
I got a message from the recovering firm that the disk heads and platters are in such a state that with the current replacement of the head assembly, it was almost impossible to retrieve any real data…But not all is lost ; there still is a chance that data can be recovered. But it will take some time and effort. Luckily it is both fixed price and no-cure-no-pay. If they succeed, tke UK holiday report can be extended with the tracking data (meaning I may have to re-generate and ere-install the album, but that’s just a matter of a few minutes :).
The replacement disk – 320 Gb – has been installed and initialized, so I’m still better off in terms of storage space.
Spam decrease
A few days ago I learned that a server that was heavily used by spam-sending botnets, was taken offline last month. That explains the downfall of the numbers of spam messages. A decrease I have observed as well. But as expected, it gradually re-increases….

