A slight change
It’s getting exceedingly problamatic to login as administartor on the blogs. It all boils down to the PHP installation and mapping, so I’ll upgrade both Wasd, PHP and WordPress as soon as possible – probably next weekend. That also means that the view of these blogs will change…Hopefully it will solve these (and other) issues; I’ve tried so using Daphne – that runs WASD 10.0.2, the lastest PHP port by Mark Berryman and WordPress 3.0.1. And since the latest vesrion seems to be 3.0.5 (shown on the banner on the admin pages) that would be a major upgrade. But the greatest chnage will be in the WASD envrionment. Luckily, it has been set up on Dahpne so it’s merely a matter op copying the files.
I hope…
To get around a few issues, I changed the design of the Trips, Tracks and Travels blog – using another theme, which loads faster – and allows login from it. The Dust Theme always required by restart of the browser, and somethimes this helped….
DDoS attempts
It has been quiet on the (D)Dos front fro some time, but this weekend there has been another attempt, from different addresse; it might have been a distributed atgtack, or ifrom one route over different anonymizers – but the addresses have been noted; action is planned.\
Fiber coming
According the plans, laying the galss fiber in our street will start this week – and within a few weeks I’ll have my FAST access. Originally I opted for a 10Mb connection, but since 50Mb (symmetrical) is not that much extra, I’ll make my move.
24-Jan-2011
More malicious attempts blocked at the gate
I expected it to happen: When one network is blocked, attempts will come from another source. So in the cause of a few days, I blocked a few more subnets. It seems to help, since the number of alerts dropped, and accessing the site is more constant and stable. I’m working on a method to report on abusive access – no matter in what way: DoS, Spam, FTP store, HTTP(s) attempts to break into software I don’t run (or on a different location). And than I’ll be able to publish them…
One package though needs closer attention, as I think chnaging it’ s locations to ReadOnly is trouiblesome, I need some advise from the specialist in that area. But I removed a possible cause of trouible – when looking to it’s name, I suspect it was – and cleaned quite a lot of rubbish tghat is must have left behind. Also, the users I previously disabled have now been deleted, and the caches cleared.
(The Dutch railways offer Internet in some of the fast trains – free until 2012, according their site. That’s where I wrote the entry)
19-Jan-2010
Bandwith management
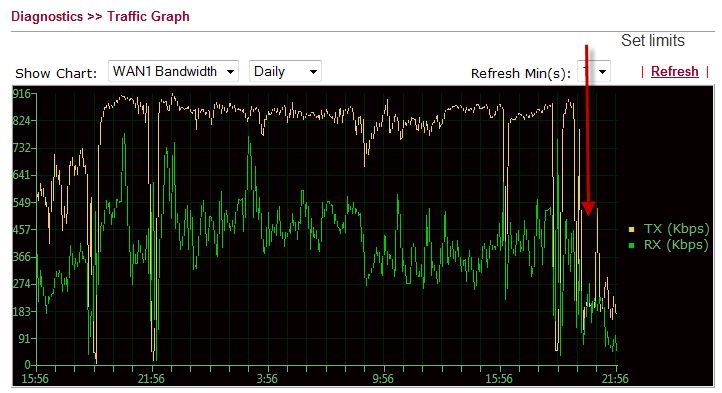
My son has bought a laptop some weeks ago and now he’s consuming all bandwidth downloading. At some point the software he uses had over 4000 sessions open, causing a severe access problem – both from outrside as inside. Most of this traffic seems to be outgoing – synchronisaton, probably?.
First, I squeezed the number of sessions from his laptop to a max of 200 – that helped somewhat, but still the outgoing traffic took almost all available space on the 1Mb channel. So this evening, I limited his upload bandwidth to 200Kb – and that caused his download speed to be much lower as well.
This shows immediately in the traffic graph:
Stupid program ….
Another side effect is that the SYSLOG files grows VERY FAST. Where it took a few days – or a week – to exceed 25000 blocks, now it took just severakl hours…Each day, the log grows to a 125.000 blocks. This squeezing may decrease the growth as well – less traffic means less entries.
Space is not a real issue, but I’ll have to keep a keen eye on the size…
Blocking abuser
Another ability the router / firewall offers is blocking access from specific addresses – or subnets. That allows me to block a complete subnet: 69.25.7.0. This network offers the possibility of DoS attacks over Trace_rt – that doe occur severely at tgimes, overfilling my mailbox by the number of alerts due tgo these attemps, from the network, ending by a number ending in a mulitple of 4. We’ll see what happens next. Of course, this blocking is logged.
BTW: The owner – according WHOIS – has been notified of the abuse. But I didn’t receive confirmation – yet.
Disk trouble – continued
I got a message from the recovering firm that the disk heads and platters are in such a state that with the current replacement of the head assembly, it was almost impossible to retrieve any real data…But not all is lost ; there still is a chance that data can be recovered. But it will take some time and effort. Luckily it is both fixed price and no-cure-no-pay. If they succeed, tke UK holiday report can be extended with the tracking data (meaning I may have to re-generate and ere-install the album, but that’s just a matter of a few minutes :).
The replacement disk – 320 Gb – has been installed and initialized, so I’m still better off in terms of storage space.
Spam decrease
A few days ago I learned that a server that was heavily used by spam-sending botnets, was taken offline last month. That explains the downfall of the numbers of spam messages. A decrease I have observed as well. But as expected, it gradually re-increases….
02-Nov-2010
Stupid…
I accessed a website I shouldn’t have accessed – but at times you’re just curious, and normally, havoc is prevented by the malware detection on the system.
Not so good, this time. But you’ll only find out when harm is done. No matter your precautions:
The site really was unsafe: it uploaded a JAVA application onto Aphrodite, that tried to access the Internet. Of course, this was blocked by the malware detection I have always running; but nevertheles, some ‘malware detection product’ seemed to be installed. The malware tracker alarmed that a trojan was encountered, and I started a scan, during which I removed some weirdly named .EXE and .JAR files on the system, dated today; the .EXE files must have been included in the .JAR files that were tansferred to the system, I’d seen the names of the executables in the intercepted traffic attempts.
The virus-scan revealed one ‘Potentially Unwanted program’ but was unable to remove it on request – asking for a reboot. And so I did.
I shouldn’t have done.
It turned out that Aphrodite didn’t boot into Windows any more. Even in a minimal mode: safe mode with command prompt. On screen, you would only see three files loaded – the last being MDCOM.DLL, and then boot stalled. No more activity at all. I could do a boot from the Windows XP installation CD, but there was no way to restore the system in a short while. The Ubuntu environment however does boot nicely, so it’s definitely a Windows problem. I looked around and it will mean I have to re-install the system in repair mode…
What will happen to the current Linux-based boot-loader, remains to be seen.
But one luck: the C-drive doesn’t contain a lot of data, and what data there is, can easily be moved off that disk. However, the Ubuntu environment does not accept the WD Passport disk on a USB port. At least, I haven’t encountered a solution to this problem.
It might be a point to reconsider XP. I do need a Windows environment (since some of the programs I use have no Linux equivalent, and the company relies on the Office suite) so I might move on and instalkl Windows7 professional – for $299 ‘only’. (I’ve checked before and the system does match the requirements – after I double the memory :))
01-Sep-2010
Cleanup
The cleaning job has run last night, and I ran into a timing problem: The operator log has been copied, a new index page was created — after which the logfiles must have been archived. So yesterdays log that could show something on the connection issue, was no longer available on-line.
Update< ./font>:I checked the operlog, and the event shows up:
%%%%%%%%%%% OPCOM 30-AUG-2010 20:20:49.75 %%%%%%%%%%%
Message from user SYSTEM on DIANA
Message from syslogd@Unknown at Aug 30 19:28:50 ...
Vigor: WAN 1 is down.
%%%%%%%%%%% OPCOM 30-AUG-2010 20:20:50.20 %%%%%%%%%%%
Message from user SYSTEM on DIANA
Message from syslogd@Unknown at Aug 30 19:28:50 ...
Vigor: WAN 1 is UP.
%%%%%%%%%%% OPCOM 30-AUG-2010 20:30:23.42 %%%%%%%%%%%
Message from user SYSTEM on DIANA
Message from syslogd@Unknown at Aug 30 19:38:20 ...
Vigor: --SendMailAlert--
The alert didn’t arrive so that is still to be settled in the router.
I would have expected a mail of last month’s mail statistics but that didn’t arrive either, so there is still something wrong.
Update< ./font>: No it’s Ok. It will show up in the log, it isn’t mailed.
Password reset requested?
I got a mail this morning from Twitter, that a new password was requested. Must have been someone else, so I accessed Twitter.com directly and changed my password. All others as well, whereever I could access the pages. But this was my intention anyway.
Update< ./font>: ALL passwords have been changed. The Bootcamp2008 blog seems to have been compromise3d, so it has been disabled – it will now render a 404 error.
Mail statistics
PMAS statistics for August
Total messages : 9140 = 100.0 o/o
DNS Blacklisted : 1875 = 20.5 o/o (Files: 31)
Relay attempts : 5940 = 64.9 o/o (Files: 31)
Processed by PMAS : 1325 = 14.4 o/o (Files: 31)
Discarded : 139 = 10.4 o/o (processed), 1.5 o/o (all)
Quarantained : 350 = 26.4 o/o (processed), 3.8 o/o (all)
Delivered : 836 = 63.0 o/o (processed), 9.1 o/o (all)
More important: on 25-August, there have been – again – a massive amount of relay attempts; the file is 564 blocks in size – 2300 lines alltogether. Second are attempts 10 days earlier, about 2100 times. These files need to be more closely examined, but on first glance, the sender’s address is known. Reason enough to block 126.com and sina.com.
By the way: the license needs to be renewed, it will expire tomorrow.