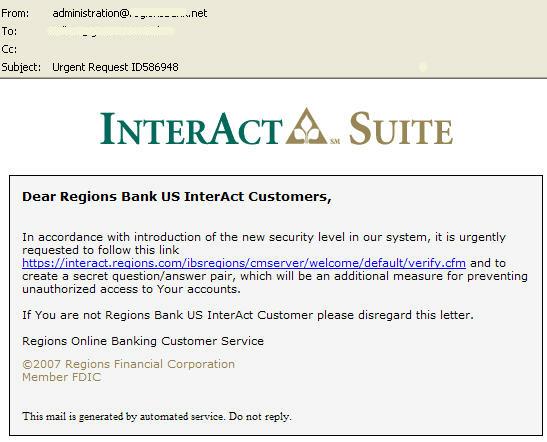
Someone has send mail around requesting you, as an Interact Suite cusomer, to help them to “enhance security”. This is how the message looks like when opened in Outlook – where it will show up as HTML page (I guess most users have it set that way):
But in raw tekst (use “View source”), it’s appears to be some other addaress:
In accordance with introduction of the new security level in our system, it is urgently requested to follow this link
<a href=”http://interact.regions.secuserver8.com/ibsregions/cmserver/welcome/default/verify.cfm”>
https://interact.regions.com/ibsregions/cmserver/welcome/default/verify.cfm</a>
and to create a secret question/answer pair, which will be an additional measure for preventing nauthorized access to Your accounts.
In order that only customers will use this abusive link, is says:
If You are not Regions Bank US InterAct Customer please disregard this letter.
A good bank has proper relation management and this letter would not have been sent in the first place!
Full header as it appears on my system:
Return-Path: akstcutahmbdmnsdgs@utahmbd.com
Received: from 198.pool85-49-20.dynamic.orange.es (85.49.20.198)
by diana.intra.grootersnet.nl (V5.6-9, OpenVMS V8.3 Alpha);
Tue, 17 Jul 2007 23:49:49 +0100 (CET)
Return-Path:
Received: from aa.bb.cc.dd (HELO utahmbd.com)
by grootersnet.nl with esmtp (C-X)*-PU0A6G 7++;+S)
id B5J@/5-152D.< -M.
for XXXXXXXXXX@XXXXXXXXXX.NL; Tue, 17 Jul 2007 21:49:44 -0100
From: "administration@XXXXXXXXXXXX.net"
To: < (Me)>
Subject: Urgent Request ID586948
Date: Tue, 17 Jul 2007 21:49:44 -0100
Message-ID: <01c7c8bc$6345e3c0$6c822ecf@akstcutahmbdmnsdgs>
MIME-Version: 1.0
Content-Type: multipart/related;
boundary="----=_NextPart_000_000A_01C7C8CD.26CEB3C0"
X-Mailer: Microsoft Office Outlook, Build 11.0.5510
X-MimeOLE: Produced By Microsoft MimeOLE V5.50.4963.1700
Thread-Index: Aca6Q7S.*N?F8/51UL9890?+F9?73)==
(for obvious reasons, I have removed email addresses – except the sender’s one. To start wityh, it looks like a complete bogus one, and if it isn’t, well, Ãt’s his own fault)
I have informed the ISP and the expected sender.
