This might be correct:
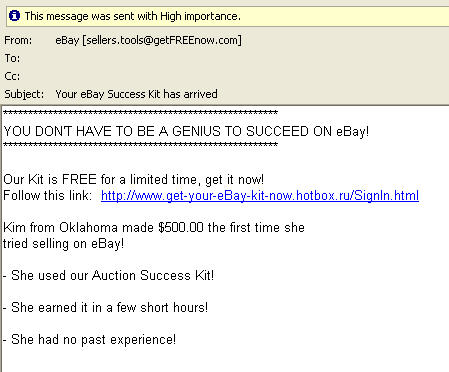
The header looks quite honest as well:
Return-Path: sellers.tools@getfreenow.com
Received: from host75-97.pool217169.interbusiness.it (217.169.97.75)
by diana.intra.grootersnet.nl (V5.6-9, OpenVMS V8.3 Alpha);
Sat, 1 Sep 2007 12:44:47 +0100 (CET)
Received: from User ([70.91.163.25])
by mail.publiposter.it (Merak 7.4.2) with ASMTP id BJV74577;
Sat, 01 Sep 2007 12:44:42 +0200
Reply-To: <no.reply@eBay.com>
From: "eBay"<sellers.tools@getFREEnow.com>
Subject: Your eBay Success Kit has arrived
Date: Sat, 1 Sep 2007 05:45:17 -0500
MIME-Version: 1.0
Content-Type: text/plain;
charset="Windows-1251"
Content-Transfer-Encoding: 7bit
X-Priority: 1
X-MSMail-Priority: High
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
but without a TO: line, and a reply-to address at ebay, makes it suspicious. As well as the user address: 70.91.163.25. This is located in the USA:
Comcast Business Communications, Inc. CBC-CM-3 (NET-70-88-0-0-1)
70.88.0.0 - 70.91.255.255
Comcast Business Communications, Inc. CBC-LITTLEROCK-4 (NET-70-91-163-0-1)
70.91.163.0 - 70.91.163.255
# ARIN WHOIS database, last updated 2007-09-01 19:10
# Enter ? for additional hints on searching ARIN's WHOIS database.
The receiving server (mail.publiposter.it) could be geniune:
Domain: publiposter.it
Status: ACTIVE
Created: 2002-06-14 00:00:00
Last Update: 2007-06-30 00:04:10
Expire Date: 2008-06-14
Registrant
Name: Publiposter & Multimedia s.p.a.
ContactID: PUBL355-ITNIC
Address: Publiposter & Multimedia s.p.a.
Isola Delle Femmine
90040
PA
IT
Created: 2007-03-01 10:39:36
Last Update: 2007-03-01 10:39:36
Admin Contact
Name: Alessio Alessi
ContactID: AA1731-ITNIC
Address: Publiposter & Multimedia s.p.a.
Isola Delle Femmine
90040
PA
IT
Created: 2002-06-14 00:00:00
Last Update: 2007-03-01 07:39:08
Technical Contacts
Name: Centro Gestione Village
ContactID: CGV35-ITNIC
Organization: Telecom Italia Spa
Address: Telecom Italia Spa
Via Pontina, km. 29,100
Roma
00040
RM
IT
Created: 2007-03-01 10:25:57
Last Update: 2007-03-06 14:04:12
Registrar
Organization: Telecom Italia s.p.a.
Name: INTERBUSINESS-MNT
Nameservers
dns6.interbusiness.it
dns3.nic.it
and interbusiness.it – also Italian – as well:
inetnum: 217.169.97.64 - 217.169.97.95
netname: IDC-DIALUP-POM-BLCK3
descr: IDC - Telecom Italia - network used in dialup access - Pomezia
country: it
admin-c: ITR2-RIPE
tech-c: ITR2-RIPE
status: assigned PA
mnt-by: FULCOM-MNT-RIPE
source: RIPE # Filtered
role: IT Telecom Role
address: Telecom Italia S.p.A.
address: Via Oriolo Romano, 257
address: Italy
phone: +390665679934(3)
fax-no: +390636870532
e-mail: ripe-noc@telecomitalia.it
remarks: trouble: ripe-noc@telecomitalia.it
admin-c: ITR2-RIPE
tech-c: ITR2-RIPE
nic-hdl: ITR2-RIPE
remarks: ##############################################
remarks: Pay attention
remarks: Any communication sent to email different
remarks: from the following will be ignored !
remarks: ##############################################
remarks: Any abuse and spamming reports, please
remarks: send them to abuse-ripe@telecomitalia.it
remarks: ##############################################
mnt-by: FULCOM-MNT-RIPE
source: RIPE # Filtered
Used in dial-up access – you can tell by the full address as well.
The domain: interbusiness.it is valid also:
Domain: interbusiness.it
Status: ACTIVE
Created: 1996-01-29 00:00:00
Last Update: 2007-01-30 00:36:13
Expire Date: 2008-01-29
Registrant
Name: Telecom Italia S.p.A.
ContactID: TELE616-ITNIC
Address: Via Paolo Di Dono, 44
Roma
00143
RM
IT
Created: 2007-03-01 10:44:12
Last Update: 2007-03-01 10:44:12
Admin Contact
Name: Camillo Di Vincenzo
ContactID: CD2-ITNIC
Address: Telecom Italia S.P.A.
Via Paolo Di Dono, 44
Roma
00143
RM
IT
Created: 2000-11-15 00:00:00
Last Update: 2007-03-01 07:49:08
Technical Contacts
Name: Domain Registration Staff
ContactID: DRS9-ITNIC
Address: Telecom Italia S.p.A.
Via Campania 11
Taranto
74100
TA
IT
Created: 2005-07-19 00:00:00
Last Update: 2007-08-08 10:51:21
Name: Gian Luca Mattu
ContactID: GLM2-ITNIC
Address: Telecom Italia SpA
Via Oriolo Romano, 240
Roma
00189
RM
IT
Created: 2005-03-09 00:00:00
Last Update: 2007-03-01 07:37:44
Name: Fabio Ginocchi
ContactID: FG82-ITNIC
Address: Telecom Italia
Via Oriolo Romano, 257
IT
Created: 2000-11-02 00:00:00
Last Update: 2007-03-01 07:38:47
Registrar
Organization: Telecom Italia s.p.a.
Name: INTERBUSINESS-MNT
Nameservers
dnsti.interbusiness.it
dns.opb.interbusiness.it
dns3.nic.it
dnsts.interbusiness.it
and makes sense because this domain is mentioned earlier – it’s name server is used.
The link in te mesage however, leads to Russia – it looks like a valid page but the contents are Russian, contains a huge amount of redirects on CGI, and the link to get an English page returns”a 404-message: Document not found.
This stinks!

