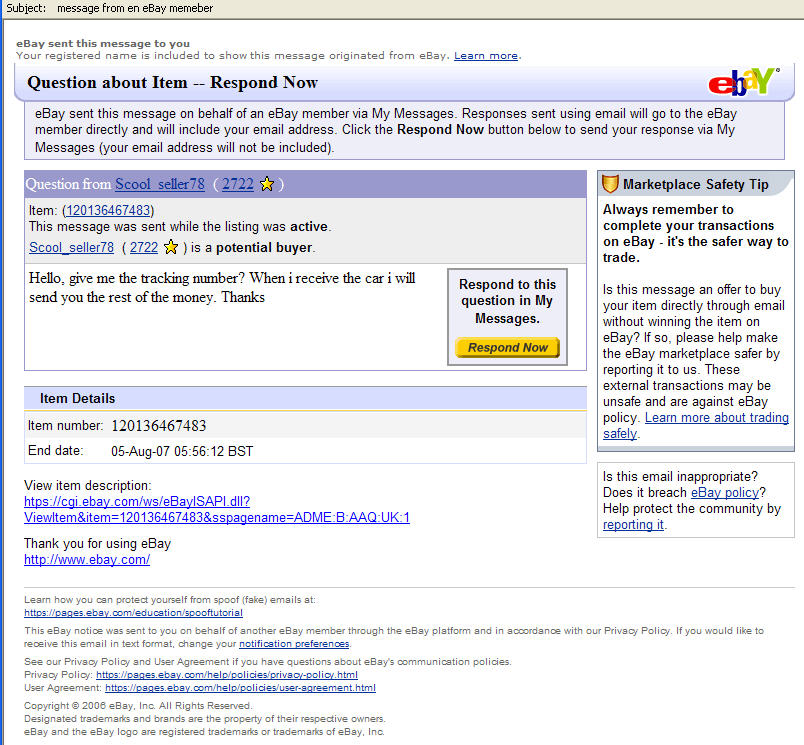
Again: this is fake since my name is not shown at the top. The message header shows the mail never had its origin at Ebay:
Return-Path: member@eday.com
Received: from datumarchitects.us (69.36.176.162)
by xxxxxxxx.grootersnet.nl (V5.6-9, OpenVMS V8.3 Alpha);
Mon, 6 Aug 2007 19:29:02 +0100 (CET)
Received: from User ([195.84.14.70])
(authenticated bits=0)
by yyyyyyyyyy.us (8.12.11.20060308/8.12.11) with ESMTP id l76HIw5B001374;
Mon, 6 Aug 2007 11:19:00 -0600
Message-Id: <200708061719.l76HIw5B001374@yyyyyyyyyy.us>
Reply-To:
From: "member"
Subject: message from en eBay memeber
Date: Mon, 6 Aug 2007 19:19:13 +0200
MIME-Version: 1.0
Content-Type: text/html;
charset="Windows-1251"
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
Content-Transfer-Encoding: quoted-printable
X-MIME-Autoconverted: from 8bit to quoted-printable by yyyyyyyyyy.us id l76HIw5B001374
(I have removed the references to innocent addresses – My guess is that the mailserver of the company mentioned as “yyyyyyyyyy.us” has been hacked, abused as a relay of that one or more machines have been infected. They have been informed.)
Besides sloppy typing (member@eDay) I don’t think Ebay will use Outlook Express.
All links in thius message lead to
<A href="http://yhandros.com/convoca/test/ws/eBay_com_Verify_your_eBay_account_files/" target=_blank>&lr;FONT color=#003399>https://pages.ebay.com/education/spooftutorial</FONT></A>
http://yhandros.com leads to a Spanish blog – in bad need for an update:
<meta name="generator" content="WordPress 2.0.1" />
Getting on with the URL: “…/convoca” leads to a form for updating files. “…/convoca/test” and, below that, “…/ws” are not accessable (Forbidden) and “…eBay_com_Verify_your_eBay_account_files/” shows an “Ebay” page to login – sending username and password to — Well, I couldn’t find out. Assuming the owner of the site has the right attitude: Either the site is hacked – or someone has uploaded the bad page up there. I did some examination of that page but couldn’t find out exactly where the submit-button leads to – it gets a cookie but I couldn’t locate it.
But when this is done deliberately – you’re warned.
UPDATE
The message to the company who’s mailserver was abused bounced back from RoadRunner .com – stating a very different address that seems to be blocked completely. That system may be abused as wel and there is no way to contact them that way.

What goes on behind the doors of the (private) data center