Once again, somone tries to get credentials using EBay-style messages.
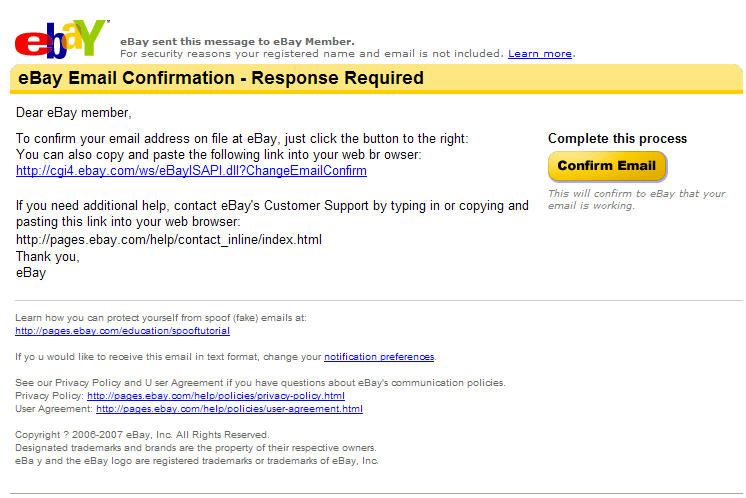
As usual, you should be alarmed by the full header:
Return-Path: member@ebay.com
Received: from mail.neel.net (71.165.245.13)
by xxxxxxxxxx.grootersnet.nl (V5.6-9, OpenVMS V8.3 Alpha);
Sat, 18 Aug 2007 20:18:13 +0100 (CET)
Received: from User ([202.28.4.25])
by mail.neel.net (Merak 7.6.2) with ASMTP id EAA74438;
Thu, 16 Aug 2007 13:13:34 -0700
From: "ebay"<member@ebay.com>
Subject: confirm your email address on file at eBay
Date: Thu, 16 Aug 2007 11:15:32 +0700
MIME-Version: 1.0
Content-Type: text/html;
charset="Windows-1251"
Content-Transfer-Encoding: 7bit
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
Outlook Express – so BASIC Internet Explorer – I’m not fooled by such stupidity.
no TO line, and the message actually states:
For security reasons your registered name and email is not included.
Makes sense – since they don’t know it. They want you to supply it to them – and your password….
The mailserver has little or nothing to do with EBay: it’s a Verizon address:
$ dig -x 71.165.245.13
; < <>> DiG 9.3.1 < <>> -x 71.165.245.13
;; global options: printcmd
;; Got answer:
;; ->>HEADER< <- opcode: QUERY, status: NOERROR, id: 17107
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 0
;; QUESTION SECTION:
;13.245.165.71.in-addr.arpa. IN PTR
;; ANSWER SECTION:
13.245.165.71.in-addr.arpa. 69628 IN PTR mail.neel.net.
;; AUTHORITY SECTION:
245.165.71.in-addr.arpa. 69628 IN NS ns2.verizon.net.
245.165.71.in-addr.arpa. 69628 IN NS ns2.bellatlantic.net.
245.165.71.in-addr.arpa. 69628 IN NS ns4.verizon.net.
245.165.71.in-addr.arpa. 69628 IN NS ns1.bellatlantic.net.
EBay may relay over Verizon or Bell Atlantic, but given the sender is from Thailand:
$ dig -x 202.28.4.25
; < <>> DiG 9.3.1 < <>> -x 202.28.4.25
;; global options: printcmd
;; Got answer:
;; ->>HEADER< <- opcode: QUERY, status: NOERROR, id: 15689
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
;; QUESTION SECTION:
;25.4.28.202.in-addr.arpa. IN PTR
;; ANSWER SECTION:
25.4.28.202.in-addr.arpa. 86400 IN PTR libmod25.lib.kmutt.ac.th.
;; AUTHORITY SECTION:
4.28.202.in-addr.arpa. 86400 IN NS libmod.lib.kmutt.ac.th.
I have my doubts.
More important: the links for your email contain a link that is NOT Ebay at all:
<div><FONT face="Arial, Verdana" size=2>To confirm your email address on file at eBay, just click the button to the right: </FONT></div> <div><FONT face="Arial, Verdana" size=2>You can also copy and paste the following link into your web browser: <BR><A onclick="return top.js.OpenExtLink(window,event,this)" href="http://0xcfead15b/signin.ebay.com/ws/index.htm"
target=_blank>http://cgi4.ebay.com/ws<WBR>/eBayISAPI.dll?ChangeEmailConfi<WBR>rm</A>
The address is coded in HEX: 0xcfead15b, and this translates to 207.234.209.91. This is the owner of the addres:
Affinity Internet, Inc AFFINITY-207-234-128-0 (NET-207-234-128-0-1)
207.234.128.0 - 207.234.255.255
Affinity Internet, Inc AFFINITY-DEDIATED-207-234-209-0 (NET-207-234-209-0-1)
207.234.209.0 - 207.234.209.255