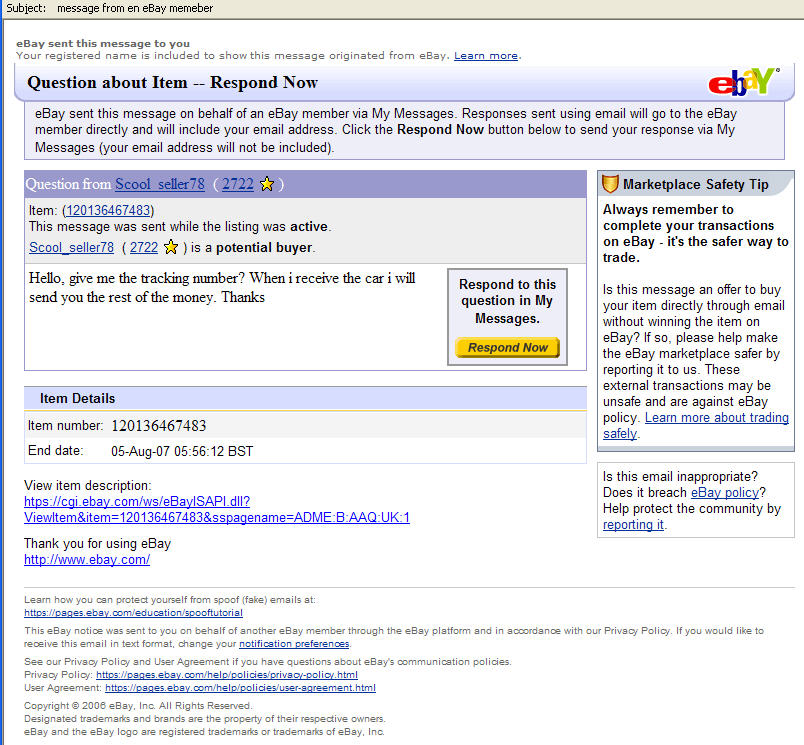
Received today:
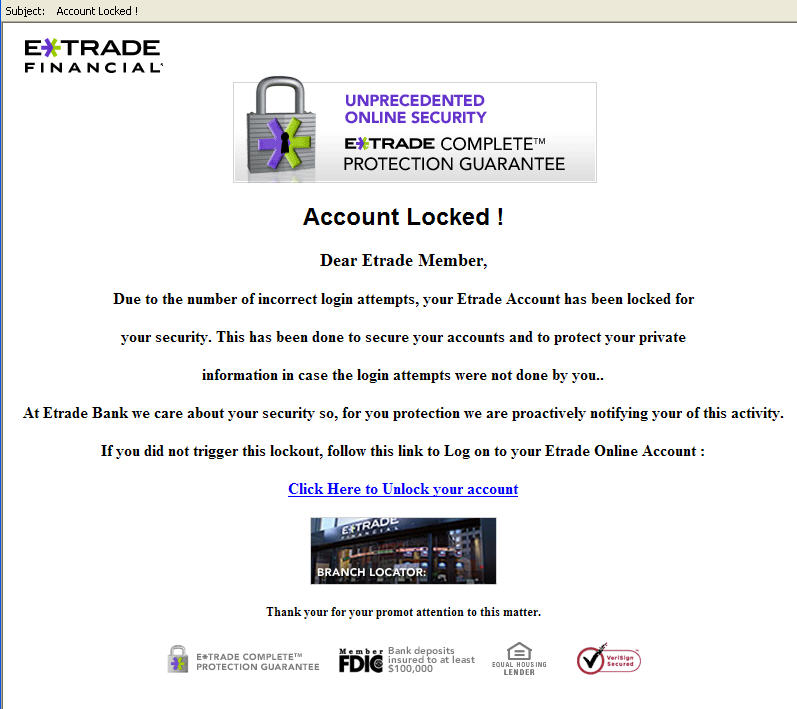
I’m not a customer, so this is moset definetly a phing attempt, doomed to fail.
The header shows it didn’t come from the bank at all:
Return-Path: service@etrade.us.com
Received: from yyy.yyy.net (203.1.13.7)
by xxxxxxxx.grootersnet.nl (V5.6-9, OpenVMS V8.3 Alpha);
Tue, 7 Aug 2007 18:24:37 +0100 (CET)
Received: from zzz.yyy.net (localhost [127.0.0.1])
by yyy.yyy.net (Postfix) with ESMTP id 442F19BBF5;
Wed, 8 Aug 2007 02:24:31 +1000 (EST)
Received: from zzz.yyy.net (unknown [192.168.0.1])
by ryyy.yyy.net (Postfix) with ESMTP id 267869BBF2;
Wed, 8 Aug 2007 02:24:31 +1000 (EST)
Received: from User ([86.107.232.208] unverified) by yyy.yyy.net with Microsoft SMTPSVC(5.0.2195.6713);
Wed, 8 Aug 2007 02:24:30 +1000
Reply-To:
From: "service@etrade.us.com"
Subject: Account Locked !
Date: Tue, 7 Aug 2007 19:24:26 +0300
MIME-Version: 1.0
Content-Type: text/html;
charset="Windows-1251"
Content-Transfer-Encoding: 7bit
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
Message-ID: <ROJANglUQgbKhR43Cdz00000e75@rojan.rojan.net%gt;
X-OriginalArrivalTime: 07 Aug 2007 16:24:30.0690 (UTC) FILETIME=[6E9D7C20:01C7D90F]
To: undisclosed-recipients:;
X-Virus-Scanned: ClamAV using ClamSMTP
and the single link in it shows a bogus address as well:
<a href="http://paperart.ro/new/etrade.us.com.php" class="style2">Click Here to Unlock your account </a>
Either a bad domain, or a kacked server? The relay is an Autralian IT company – and they have been informed (their server names and domain have been obscured)